Introduction
In this tutorial, we are going to set up a small network of 3 machines, then install and export an FTP service and then sniff all incoming packets to alert any packet transmission from the outside that does not include service exported to the network (FTP). For this purpose, the work is divided into three parts: we will start by installing an FTP service and make it available to users inside and outside the LAN.
We will also put a signaling mechanism of any attempt to access from the outside to any application outside of FTP using Snort rules.
LAN
Here is the local network used for this experiment. The network installed here is a little different because it is just a subset of 3 machines in a bigger network. Here is the topology we are going to use:
IP addresses assigned to machines are summarized in this table.
| Equipment | IP Address | Interface | Default Gateway |
| Firewall / IN & OUT | 192.168.106.179/24 | eth1 | Dhcp |
| Post LAN | 192.168.106.172/24 | eth0 | Dhcp |
| FTP | 192.168.106.171/24 | eth0 | Dhcp |
| External machine | 192.168.106.128/24 | wlan0 | Dhcp |
Interface Configuration
For the basic configuration of the network, we will use the DHCP service. So for all machines in this configuration, we have an IP address for a certain leased period. The addresses obtained by DHCP are those summarized in the table above and will be used throughout this experiment.
FTP server configuration
We will install an FTP server to enable internal and external users of the LAN to perform file transfers. We can perform this installation by using the synaptic package manager or by using the command apt-get install for the following packages:
proftpd-basic, proftpd-mod-ldap, proftpd-mod-pgsql proftpd-mod-mysql
After installation we can locally test the proper functioning of the server.
Firewall Configuration
A firewall is a network component, which acts as a barrier to control all traffic, in or out of the network. It allows you to block unauthorized access and allows only authorized communication. But in our case, we will not block anything. We will implement in the firewall some simple rules whose sole purpose is to redirect FTP requests to the FTP server. Thus external users can do FTP through the firewall which will act as an intermediary between the client and the server located in a machine on the LAN.
To implement this mechanism, we will use iptables and define rules for the firewall management.
Enable routing
Enable the firewall to act as router and gateway for the transmission of
packets on the LAN machines.
echo 1> / proc/sys/net/ipv4/ip_forward
• IP Address Translation
This refers to all machines on the local network to masquerade as the firewall to exit the local network, this is necessary for the FTP server for all responses and requests received from outside the firewall must go through the firewall, and the firewall will respond by going to the FTP server.
iptables -t nat -A POSTROUTING -o eth1 -j MASQUERADE
The semantics of this command is as follows: After determining the route of package, the firewall will change the sender address before sending the packet to outside the network.
• Redirect incoming FTP requests to the FTP server
No service is available or implemented on the firewall machine, so for each query that happens, the firewall must redirect to the server responsible for responding to query type. So here we'll redirect all requests to the FTP port to the FTP server at 192,168,106,171.
iptables -t nat -A PREROUTING -j DNAT -i eth1 -p tcp --dport 21 --to-destination 192.168.106.171
One can notice the keywords as PREROUTING that tells the firewall to forward packets addressed to port 21 to the post address 192.168.106.171.
For the FTP server to operate properly, additional rules must be added. In fact, most FTP servers use other ports that allow for customers to switch to passive mode, which corresponds to the mode of data transfer. These ports are configured as an interval at the FTP server in the file /etc/proftpd /proftpd /conf. To do this, simply uncomment the following line:
PassivePorts 49152 65534
We'll also make a redirection of previous requests on these ports.
iptables -t nat -I PREROUTING -p tcp -i eth1 --dport 49152:65534 -j DNAT --to
192.168.106.171:49152-65534
• Allow any other input communication.
As we said earlier, everything is allowed for everyone, so we have allowed all communications input and output. So the firewall will receive all requests and respond if possible. All that will save it in log files all external communications that are not FTP requests.
iptables-P INPUT ACCEPT
iptables-P OUTPUT ACCEPT
Another precaution to take to enable the FTP server to work for all external accesses, we must indicate the IP address of the firewall to the FTP server to make the address translation possible. This is once again in the file /etc/ proftp/proftp.conf by ensuring the existence of the following line.
MasqueradeAddress 192.168.106.179
Snort Rules
In this section, we discuss the configuration of snort application, to enable the detection of suspicious transactions. The policy of this detection is as follow:
For users inside the network: Everything is allowed, hence no control and no
alert in the internal network.
For users outside the network: only the FTP service is permitted with no control, therefore
all requests to another service will be saved as alerts.
To implement this policy, we will use snort rules. We will firstly alert all packets on a TCP port other than FTP ports from outside, and secondly we will alert all udp and icmp queries from outside.
• TCP Alerts
It is important to know the ports involved in the FTP transport because, it does not use only the port 21. FTP also uses control ports (30000:49152) and ports necessary to transfer in passive mode (49152:65534). In definitive, in our snort rules we must include on behalf of FTP ports the interval: 21,30000:65534.
alert tcp ![192.168.106.171,192.168.106.172] any -> 192.168.106.179 ![21,30000:65534] (msg:“EXTERNAL TCP ACCESS”; sid:400; rev:1;)
This is to alert all incoming packets at the firewall with a different port than the ports used by FTP and providing from a machine that does not belong to the local network identified here by the two machines [192.168.106.171,192.168.106.172].
• UDP Alerts
This is to alert all incoming packets at the firewall using the UDP protocol and providing from a machine that does not belong to the local network identified here by both machines [192.168.106.171,192.168.106.172].
alert udp ![192.168.106.171,192.168.106.172] any -> 192.168.106.179 any (msg:“EXTERNAL UDP ACCESS”; sid:401; rev:1;)
• ICMP Alerts
This is to alert all incoming packets at the firewall using the ICMP protocol and providing from a machine that does not belong to the local network identified here by both machines [192.168.106.171,192.168.106.172].
alert icmp ![192.168.106.171,192.168.106.172] any -> 192.168.106.179 any (msg:“EXTERNAL ICMP ACCESS”; sid:402; rev:1;)
Thus even the ping will be alerted.
Tested And Results
Here we are going to directly see how snort reacts to different types of transmissions. We must first of all, start the snort application to listen on interface eth1 of the firewall, with our file of rules as input.
Cmd: snort-v-i eth1-c tpsnort.rules
Local machine
We used the ping and ftp commands to test the behavior of snort with TCP and ICMP traffic.
• Ping
After running the command ping 192.168.106.179 from the local station with the address 192 168 106 172 (we stopped the ping after 9 packets sent)
Here are the statistics obtained from snort.
We note that the firewall has responded to all the requests sent without triggering
no warning.
• Ftp
Similarly, after running the command ftp -p 192.168.106.179 from local machine at 192,168,106,172, we initiated a connection with an existing user. Here is an overview of commands executed.
Here are the statistics obtained from snort.
Similarly, we find that the FTP server responded to requests sent to through the firewall but without triggering any alarm. This is normal because the FTP service is never alerted. Whether when approached from the outside or inside the network.
Distant machine
Similarly, we will use the ping, ftp and ssh to see the behavior of snort.
• Ping
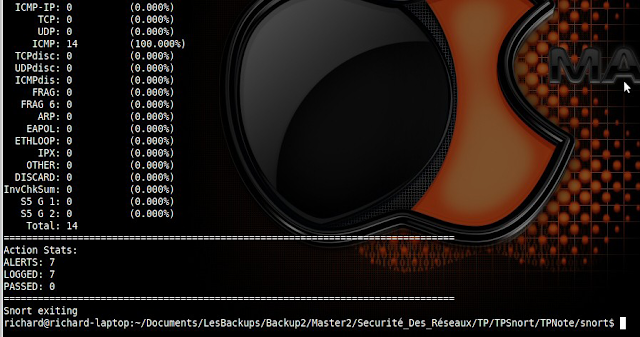
After running the command ping 192.168.106.179 from an external machine with
address 192 168 106 128 (we stopped the ping after 7 packets sent)
Here are the statistics obtained from snort.
We note that the firewall has responded to the requests sent and also triggered alerts for each packet which is normal because only the external FTP requests are not alerted. For more information about cached packets, we can read the log from snort
/var/ log/snort /alert where we can see information on five packages.
Here is a sample of packet.
[**] [1:402:1] "EXTERNAL ACCESS ICMP [**]
[Priority: 0]
01/18-19: 29:31.414249 192168106128 -> 192168106179
ICMP TTL: 64 TOS: 0x0 ID: 0 IpLen: 20 DgmLen: 84 DF
Type: 8 Code: 0 ID: 25627 Seq: 10 ECHO
• Ftp
Similarly, after running the command ftp -p 192,168,106,179 from an external machine with address 192.168.106.128. We performed the same operations as previously.
Here are the statistics obtained from snort.
We note that the firewall has responded to all the requests sent without triggering no warning. This is normal.
• Ssh
We here wanted to see the behavior of snort against another type of TCP packet
other than FTP. We attempt a connection to this server ssh at the firewall.
Here are the statistics obtained from snort.
We note that the firewall has responded to requests sent and also triggered alerts for each packet which is normal because only the FTP requests are not alerted from outside. We can also check the log and we will see packets of like this.
[**] [1:400:1] “EXTERNAL TCP ACCESS” [**]
[Priority: 0]
01/18-19:47:22.618458 192.168.106.128:47822 -> 192.168.106.179:22
TCP TTL:64 TOS:0x0 ID:57949 IpLen:20 DgmLen:60 DF
******S* Seq: 0x3045FB1A Ack: 0x0 Win: 0x16D0 TcpLen: 40
TCP Options (5) => MSS: 1460 SackOK TS: 399687 0 NOP WS: 6
Hence we can conclude that our firewall and the snort application runs
exactly as we wanted.
Conclusion
At the end of this work, which involved using the snort application to perform a basic detection of suspicious behavior in a network, it is clear that given the risk of leakage, securing a network is a task not taken lightly. In effect, with Snort, we can specify rules that allow us to analyze each packet entering the network and trigger alerts if necessary with specific messages describing the observed behavior. This is important for all network administrators because, this way they can have a global view of all transmissions performed within the network.











Thanks for sharing such a nice stuff about LAN Network Monitoring. Thanks for your valuable input. keep sharing.This is beneficial for us...
ReplyDeleteThis is amazing to read about snort for networking. The technology is making all the new trends in the world that is useful for the people.
ReplyDeleteYou blog post is just completely quality and informative. Many new facts and information which I have not heard about before. Keep sharing more blog posts.
ReplyDeleteangularjs Training in bangalore
angularjs Training in btm
angularjs Training in electronic-city
angularjs Training in online
angularjs Training in marathahalli
This is a nice post in an interesting line of content.Thanks for sharing this article, great way of bring this topic to discussion.
ReplyDeletepython training Course in chennai | python training in Bangalore | Python training institute in kalyan nagar
I have picked cheery a lot of useful clothes outdated of this amazing blog. I’d love to return greater than and over again. Thanks!
ReplyDeleteData Science Training in Chennai | Data Science course in anna nagar
Data Science course in chennai | Data science course in Bangalore
Data Science course in marathahalli | Data Science course in btm layout
This blog really pushed to explore more information. Thanks for sharing.
ReplyDeleteSelenium Training in Chennai
selenium testing training in chennai
iOS Training in Chennai
French Classes in Chennai
cloud training in chennai
web designing training in chennai
best big data training in chennai
Loadrunner Training in Chennai
Thank you for this information on network monitoring as i am associated with an IT company which provides web server monitoring in USA
ReplyDelete.Please keep sharing
I got here much interesting stuff. The post is great! Thanks for sharing it! Computing Techniques
ReplyDeleteInformative post indeed, I’ve being in and out reading posts regularly and I see alot of engaging people sharing things and majority of the shared information is very valuable and so, here’s my fine read.
ReplyDeleteclick here examples
click here en espanol
click here email virus
click here email
click here em português
nice..
ReplyDeleteinplant training in chennai
inplant training in chennai
inplant training in chennai for it
hosting
india hosting
india web hosting
iran web hosting
technology 11 great image sites like imgur hosting
final year project dotnet server hacking what is web hosting
macao web hosting
Thanks a lot for sharing this amazing knowledge with us. This site is fantastic. I always find great knowledge from it. HPAT Acer
ReplyDeletewhenever I am feeling boring I am not playing some kinds of games but on the opposite, I am starting to find some blogs where I can find helpful articles but I am not commenting there but this article really is an awesome article I ever say thanks for sharing it with us.
ReplyDeletewe have the best web designers & logo designers if you want a logo & website for your business with a guarantee visit us?
Logo Designers
Such a wonderful article.
ReplyDeleteThank you for the share with us.
best doodledoos
Learn anytime with flexible Salesforce CPQ training online. Gain real-time experience in product rules, workflows, and quoting automation. Great for beginners and working professionals.
ReplyDelete